SSO Group Mapping
Automatically translated
With Group Mappings, owners and admins can link groups from their identity provider (IdP) to the organizations and roles in DeepCloud. In this way, the assignment of SSO users to the DeepCloud organisations can be managed centrally in the IdP instead of having to do this manually in DeepCloud. This simplifies user administration and increases consistency and security.
Group mappings allow you to connect groups from your IdP to the corresponding organizations and roles in DeepCloud. When an SSO user logs in, DeepCloud automatically assigns the configured organisations and roles that have been assigned to the user’s security groups.
The management of organisations and roles for your SSO users is thus controlled by the IdP, creating a central source of truth.
Before you can set up Group Mappings in DeepCloud, your IdP must be configured to transmit users’ group information during SSO authentication.
Prerequisites
Microsoft Entra (Azure)
Configuration IDP
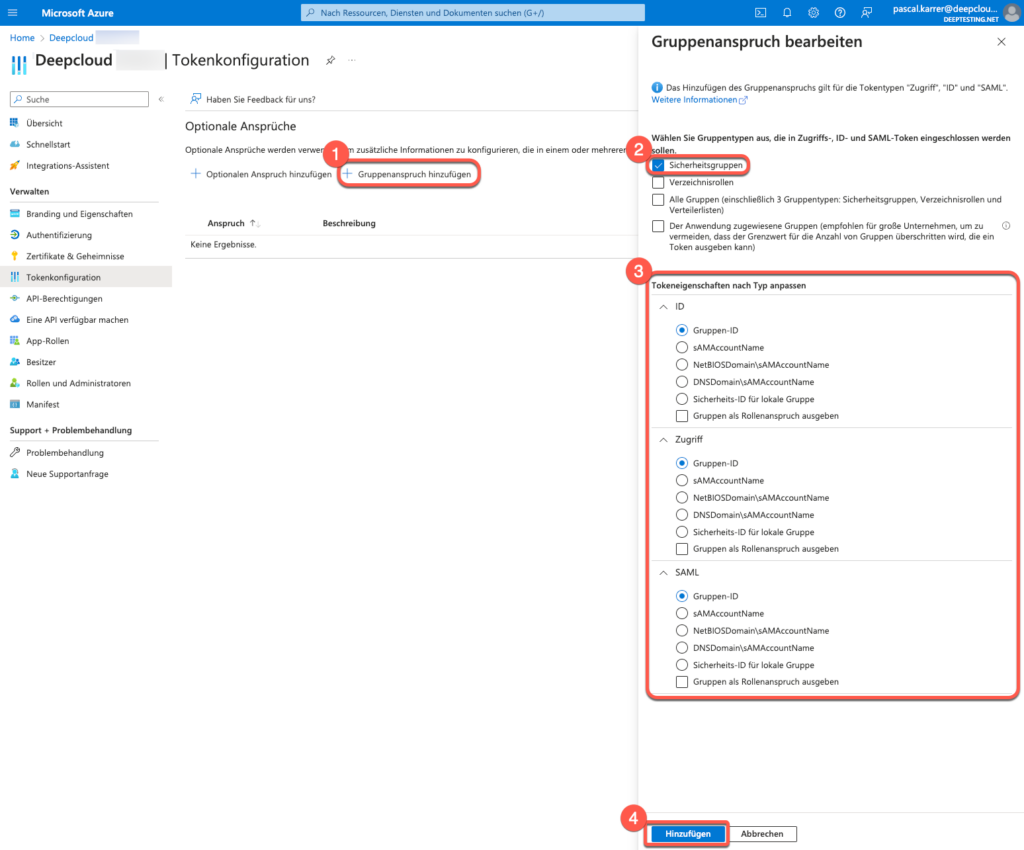
- Search for the DeepCloud App registrations in the Azure portal
Go to the Azure portal and navigate to Azure Active Directory > Microsoft Entra ID > App registrations. Search for your DeepCloud application and select it. - Select the Token configuration option in the navigation bar
- Click on Add group claim. The “Group claim” dialog box is displayed.
a. Select “Security groups” as the group type. - Select Group ID to use the unique group identifier. With this selection, the group mapping can be created in DeepCloud using the object IDs (e.g. efa39f24-e8db-4526-b65d-cc029d874c3c).
OKTA
Configuration IDP
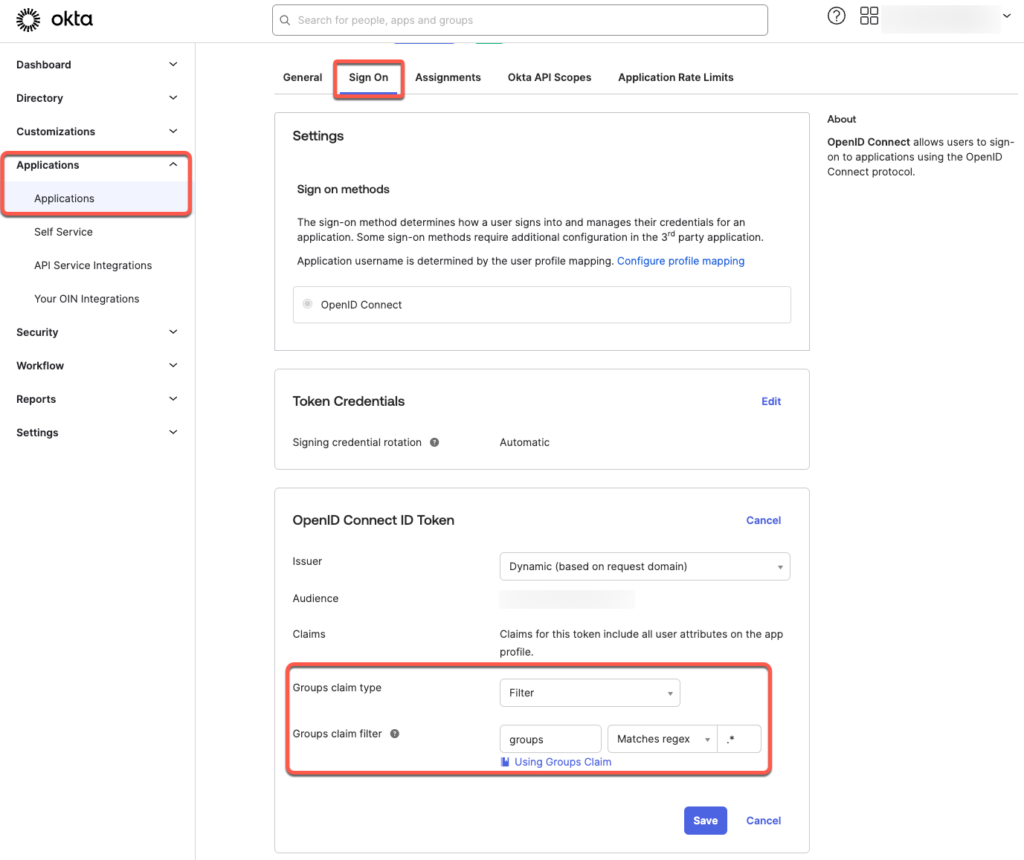
- In the Okta Admin Dashboard, search for the DeepCloud application
Go to the Okta Admin Dashboard and navigate to Applications > Applications. Search for your DeepCloud application and select it. - Select the Sign On option in the navigation bar
- Under OpenID Connect ID Token, click on Edit.
a. For “Groups claim type”, select Filter
b. For “Groups claim filter”, select “groups” “Match Regex” “.*” - Save the changes
To ensure that OKTA sends the group claims in the ID token, follow these steps:
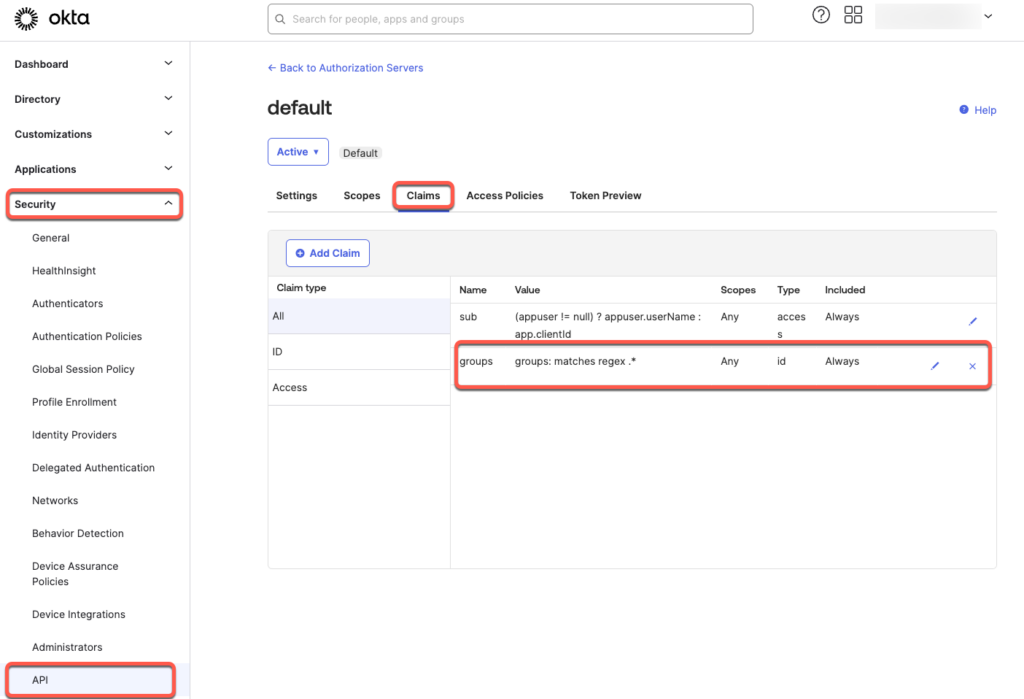
- Navigate to Security > API.
- Select the desired Authorization Server that you want to use for the DeepCloud application. Normally this is the “default”
- Click on the Claims tab.
- Add a new group claim
a. Click on the “Add Claim” button.
b. Give the claim the name “groups”.
c. Select “ID Token – Always” as the Token type
d. Select “Groups” as the Value type
e. Select “.*” for the filter “Matches Regex” - Save the adjustments
Configuration Group Mapping in DeepCloud
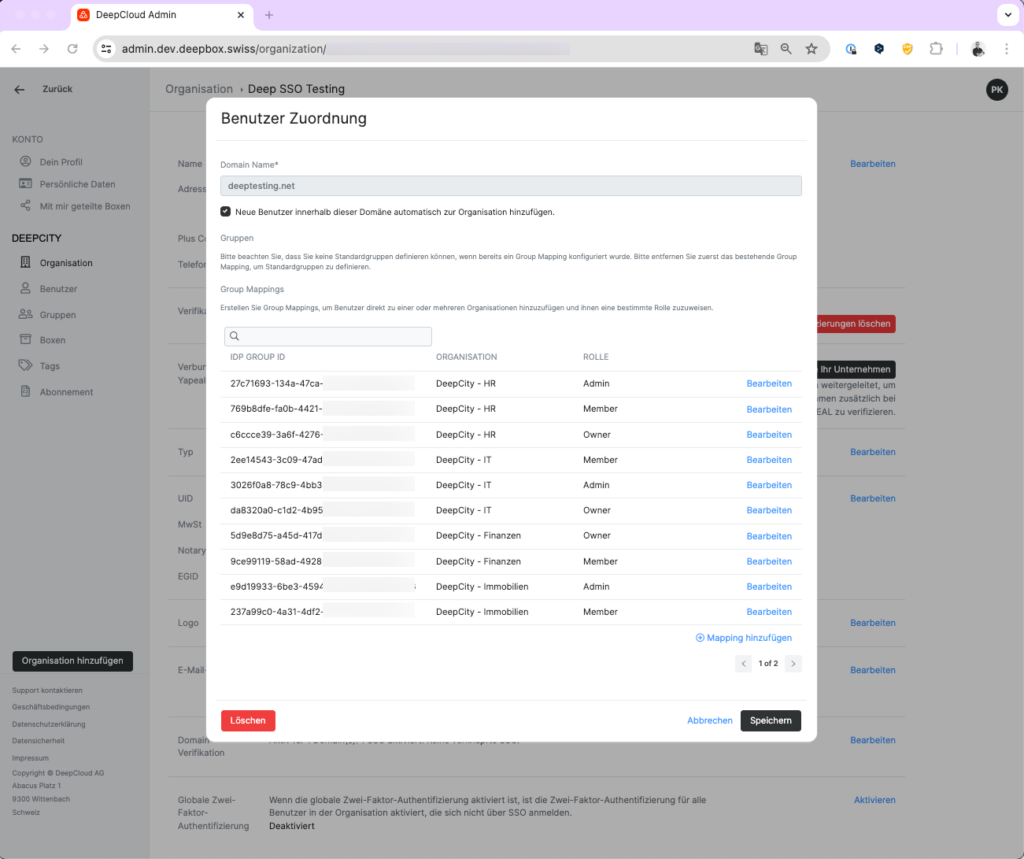
- Open the domain/SSO configuration
Go to DeepAdmin and navigate to Organization > Domain Verification / SSO Configuration > Edit. The “Domain Verification / SSO Configuration” dialog is displayed. - Select Access management to edit or create the group mapping. The “Access management” dialog is displayed.
a. Activate the “Automatically add users of this domain to the organization when logging in” checkbox. - Configure a new group mapping via “Add mapping”.
a. Enter the object ID of the security group from Microsoft Entra ID or the group name from Okta Admin.
b. Select the corresponding organization
c. Select the corresponding roles.
Note
Please note that you cannot define a group mapping if a standard group has already been configured. Please remove the existing standard groups first in order to define a group mapping.
Limitations
DeepCloud supports login tokens that contain up to 200 group IDs (OKTA up to 100 groups). If you would like to use more than 200 groups per user, please contact our support team.
Did this answer your question?
Related articles
SSO configuration
As the owner or admin of your organization, you have the option of configuring an IdP for your DeepCloud organization. This has the advantage that all users who log in with the ...
What can I do with groups?
You can add multiple users to a group and reflect teams within an organization. This is particularly helpful when working with many different boxes. This means that you don’t...

