Limit group claims to selected groups
Automatically translated
In Azure AD (Microsoft Entra ID), group memberships can be included in the token of an enterprise application in order to control authorizations within the application.
However, as Azure AD only transfers up to 150 groups directly in the token, it makes sense to limit the scope of the group claims.
If a user is a member of more than 150 groups, this can lead to group information no longer being included in the token – which can result in missing authorizations in DeepCloud.
In this article you will learn how to:
- Add groups to an enterprise application, and
- configure the group claims,
so that only the relevant (DeepCloud-related) groups are included in the token
Prerequisites
Before you start, make sure that the following points are fulfilled:
Restrict group claims to DeepCloud-relevant groups
To ensure that only the groups relevant for DeepCloud are included in the token, proceed as follows:
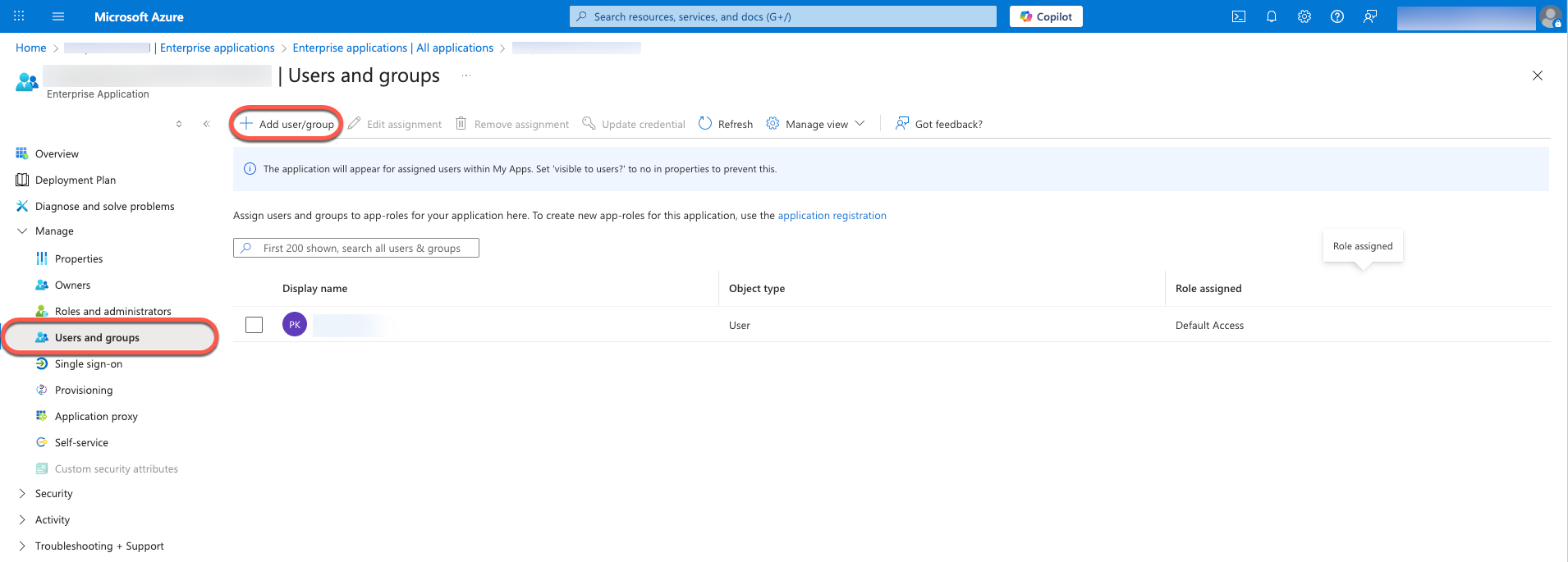
1. assign relevant groups
- Open the Azure portal: https://portal.azure.com
- Navigate to
Azure Active Directory → Enterprise Applications - Select the corresponding Enterprise application (e.g. DeepCloud).
- Open the Users and Groups menu on the left.
- Click on + Add user/group.
- Select the DeepCloud-relevant groups.
- Click on Assign to add the groups
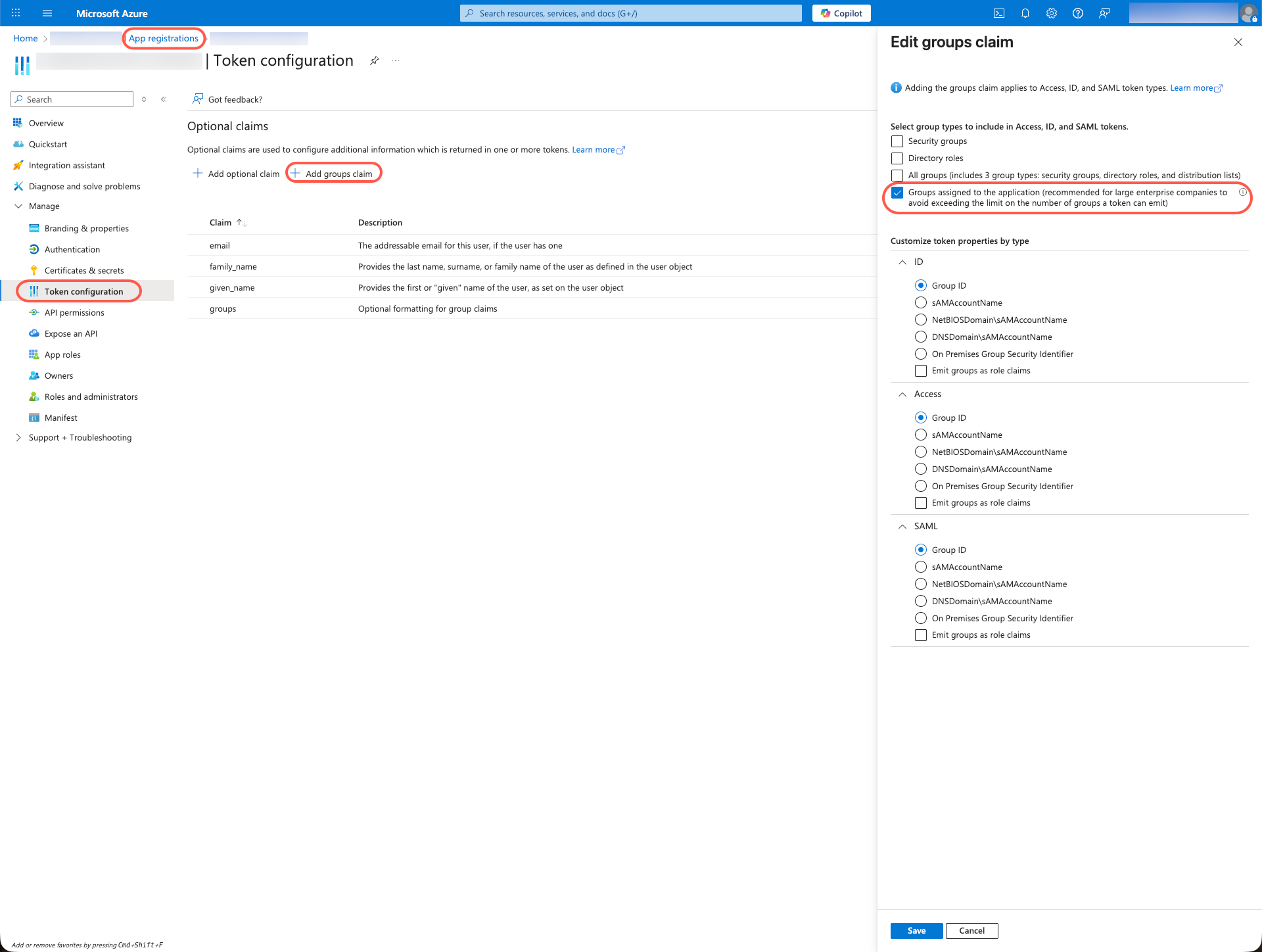
2. configure group claims
- In the Azure portal, navigate to
Azure Active Directory → Appregistrations. - Select the relevant app registration (client application).
- Go to Manage → Token configuration
- Click on + Add group claim.
- Select in the dialog:
- Groups assigned to the application
(Recommended for large companies in order not to exceed the group limit in the token).
- Groups assigned to the application
- Click on Save.
Result
After this configuration, the ID or access token will only contain the group IDs of the assigned DeepCloud groups.
This keeps the tokens lean, the Azure limits are respected and the DeepCloud authorizations are correctly maintained.
Did this answer your question?
Related articles
SSO configuration
As the owner or admin of your organization, you have the option of configuring an IdP for your DeepCloud organization. This has the advantage that all users who log in with the ...
SSO Group Mapping
With Group Mappings, owners and admins can link groups from their identity provider (IdP) to the organizations and roles in DeepCloud. In this way, the assignment of SSO users to ...
Domain claiming
Verify your domain to simplify the onboarding of new users As the owner or admin of your organization, you have the option of claiming domains (e.g. deepbox.swiss) for your ...

